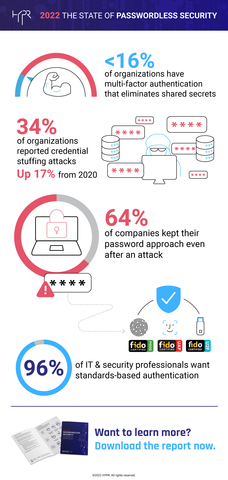
New report reveals fewer than 16% of organizations have deployed an MFA solution that eliminates shared secrets and supports a strong Zero Trust strategy
A new report from HYPR, The Passwordless Company™ and Cybersecurity Insiders, reveals that despite the Zero Trust initiative, many organizations are still highly exposed to credential attacks due to insufficient multi-factor authentication (MFA) methods and overall lack of urgency after potential exposure. In fact, 64% of those hacked did not enhance or improve their authentication controls following the attack. The findings also revealed that the perpetual cyber risk of remote work continues to drive passwordless adoption amongst organizations on a global scale.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20220208005023/en/
The State of Passwordless Security - 2022 (Graphic: Business Wire)
The “The 2022 State of Passwordless Security” report includes insights from more than 400 security and information technology professionals. It uncovers the state of conventional and passwordless authentication, key drivers, and barriers to adoption as well as overarching technology preferences, based on data from Cybersecurity Insider’s 500,000-member community.
A key finding from the report highlighted that 89% of survey respondents experienced a phishing attack against their organization in 2021, and more than a third (34%) experienced credential stuffing, a 17% uptick from the same survey conducted last year. Responses indicated a 33% rise in push attacks, with 12% of organizations reporting weaponized push notifications as the method of hack – revealing the continued target on remote employees. Despite the increasing number of breaches, only 35% believe their current authentication solution is fully secure. Additionally:
- 64% of those hacked did not enhance or improve their password-based authentication controls following the attack
- 65% of those that claim to be passwordless continue to employ methods based in secret-sharing, such as SMS or one-time password (OTP); 19% are unsure whether their solution is truly “passwordless”
“Organizations are grappling to implement a solid security strategy to meet regulations, and to ensure customer confidence, all while responding to a forever-hovering pandemic that’s leaving their teams understaffed and overworked. Many of these organizations are relying on traditional authentication methods to tick a box in the hopes it protects them against the next breach; instead, what our report reveals is that traditional MFA is creating a false sense of security,” said Bojan Simic, co-founder, CEO and CTO of HYPR. “Yet, we are seeing an uptick in awareness and understanding of the need to go beyond MFA and the overall benefits of passwordless authentication, especially in sectors such as finance and insurance. As organizations continue to roll out their Zero Trust programs, we can expect passwordless MFA to be a critical component of any security framework.”
Other key findings include:
Traditional MFA is falling short for most organizations
Multi-factor authentication spending and overall adoption is on the rise, following regulatory pressures from global initiatives, specifically the Zero Trust IT security model – but reluctance remains prominent. Nearly half (49%) cite poor user experience as a major obstacle for traditional MFA adoption, closely followed by 48% stating lack of system interoperability and integration, and cost rounding out the top three with 42%. In terms of password-MFA, many deemed the method as more of a burden, creating a greater impact on overall productivity. For example, 63% shared they were unable to access work critical information after failing to remember a password.
Organizations understand the need to go passwordless
In response to the damaging cyberattacks of 2021, coupled with work from home becoming a permanent option, more organizations are shifting to passwordless MFA. In fact, 25% of small-to-medium businesses (SMBs)[1] and similarly 34% of enterprises that kickstarted a passwordless initiative in 2021 with HYPR, were in the finance and insurance sector. The manufacturing sector was the second-largest adopter at 13%.
Most of the respondents (82%) believe strengthening their authentication security program is the major driver for passwordless MFA adoption. Contrary to traditional MFA, improved user experience followed as the second most important factor at 67% - a 5% increase from the previous year. Meeting regulatory compliance was also of notable importance at 40%. Additionally, of those companies that are passwordless:
- Remote employees are the primary users of passwordless methods (86%).
- Onsite employees follow closely at 73%, demonstrating that many organizations are employing a hybrid work model.
For more information about HYPR, visit https://www.hypr.com.
About HYPR
HYPR is a leader in Passwordless Multi-factor Authentication (MFA).
We protect workforce and customer identities with the highest level of assurance while enhancing the end users’ experience. Our approach shifts the economics of attack and risk in the enterprises' favor by replacing password-based MFA with Passwordless MFA.
With HYPR, customers can finally enable cross-platform desktop MFA, stop phishing, and reduce fraud associated with weak or stolen passwords.
Welcome to The Passwordless Company®. It’s time to reimagine identity security.
About Cybersecurity Insiders
Cybersecurity Insiders is a 500,000-member platform delivering unique, community-sourced cybersecurity research and educational content to the IT Security ecosystem, including market studies, webinars, product reviews, awards, and more. More information: https://cybersecurity-insiders.com
[1] Defined as 500 or fewer employees
View source version on businesswire.com: https://www.businesswire.com/news/home/20220208005023/en/
Contacts
Media:
Fabienne Dawson
fabienne@hypr.com
917.374.6860
Diandra Binney
Peppercomm for HYPR
dbinney@peppercomm.com
